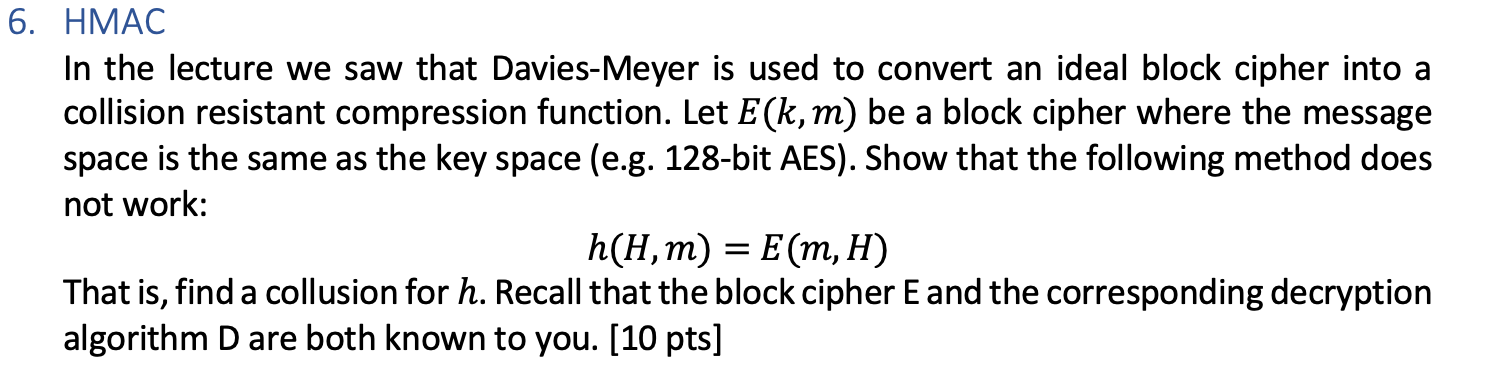
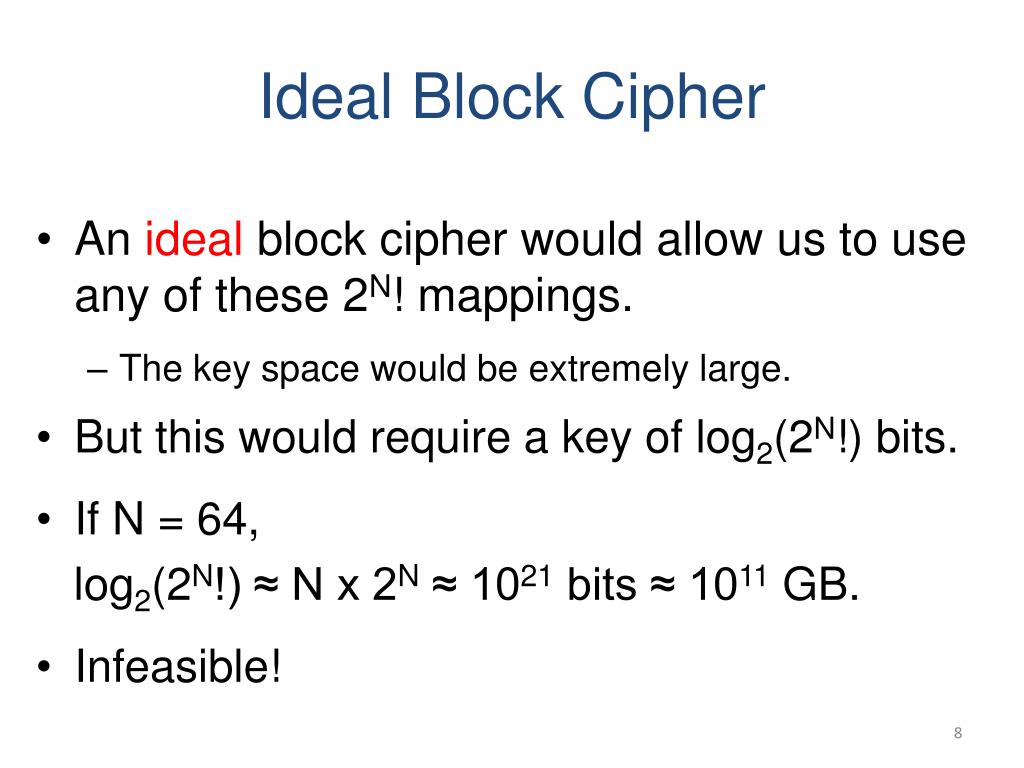
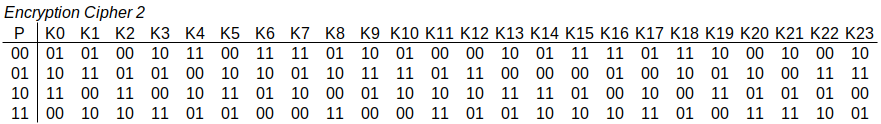
Cryptography and Network Security Block Ciphers and DES, and modes of operation M. Sakalli Reviewed, from Stallings. - ppt download
Lecture 3 Feistel based algorithms. Today 1.Block ciphers - basis 2.Feistel cipher 3.DES 4.DES variations 5.IDEA 5.NEWDES. - ppt download
2170709 Information and Network Security-Notes PDF-Unit-2 - Block Cipher Principles Stream Cipher - Studocu