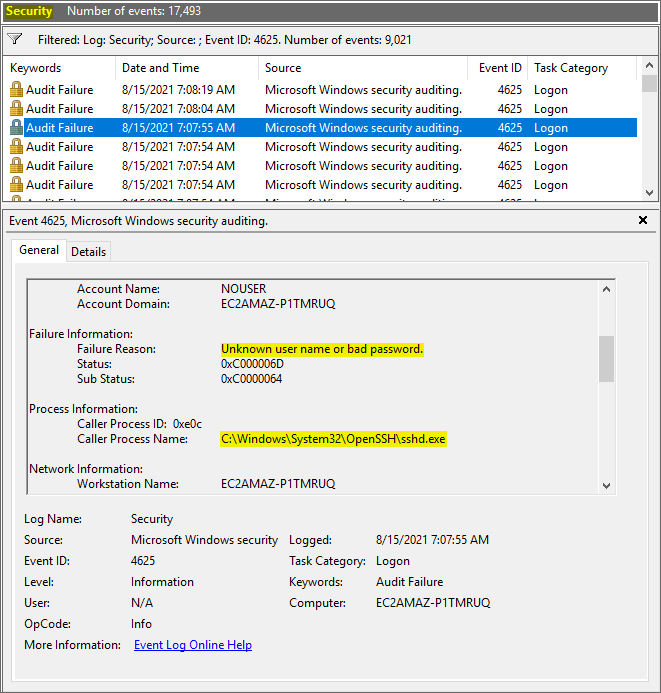
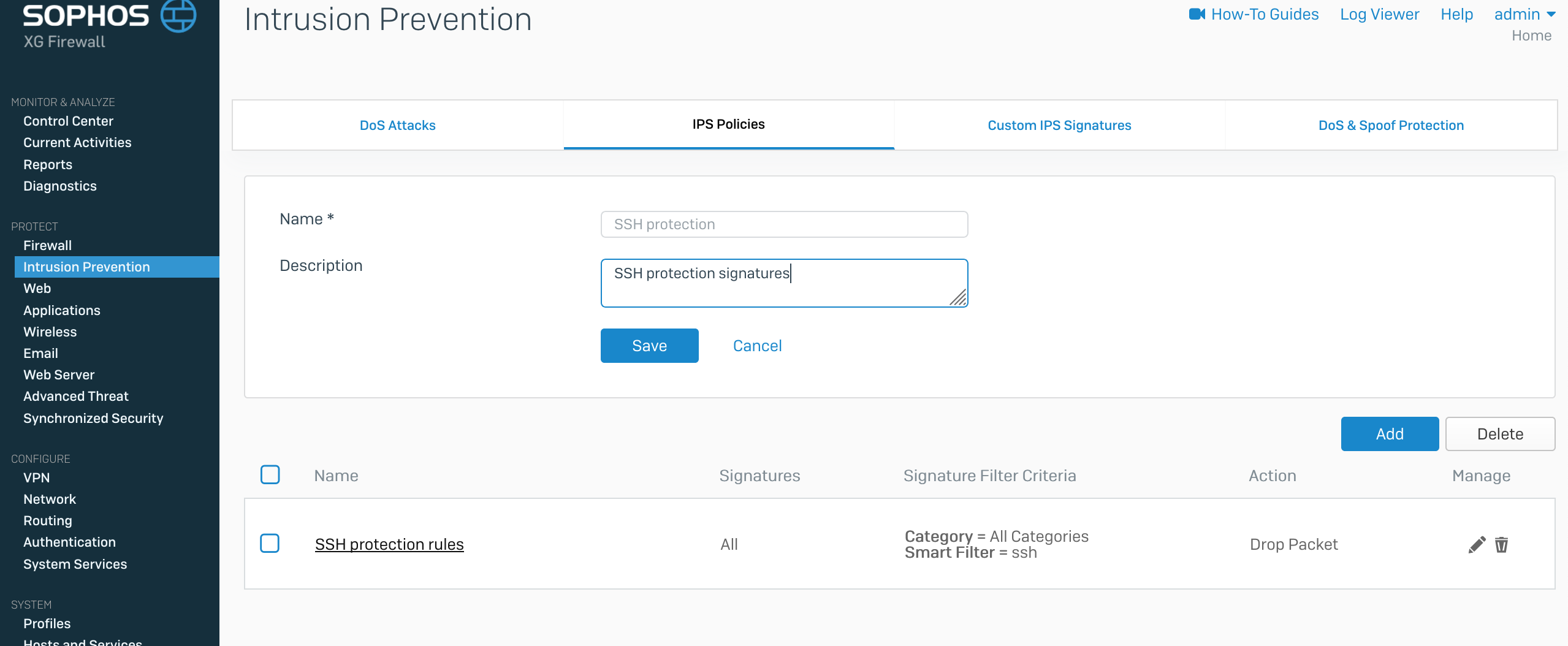
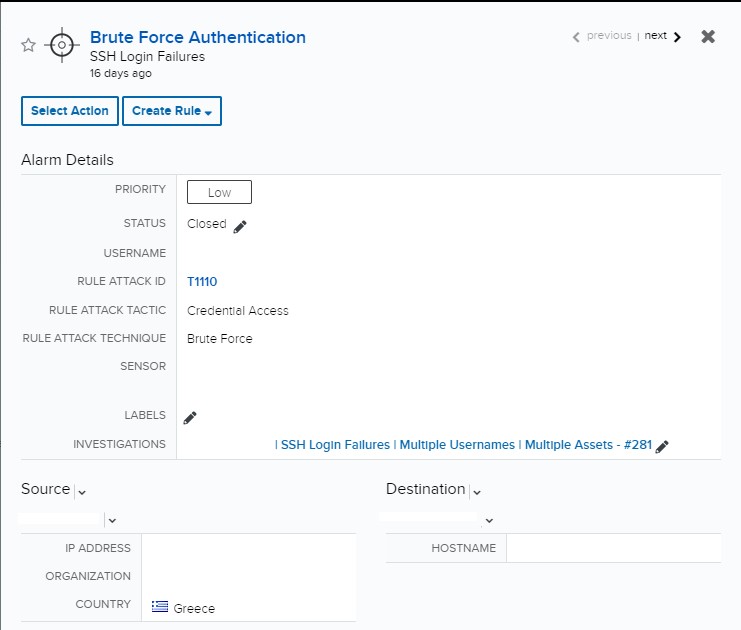
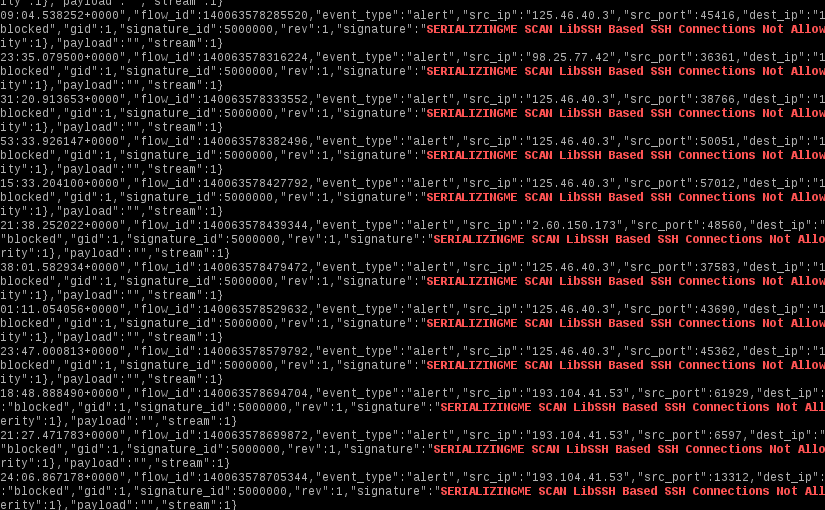
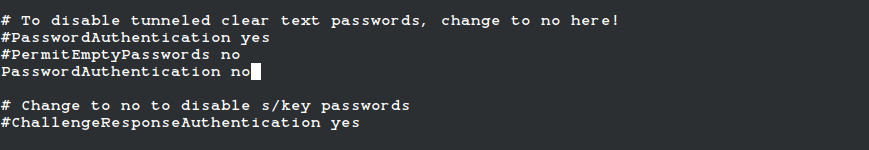
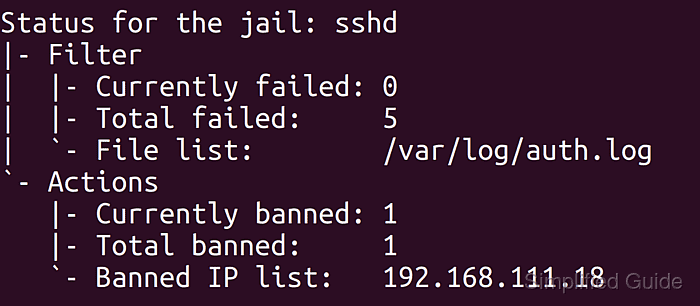
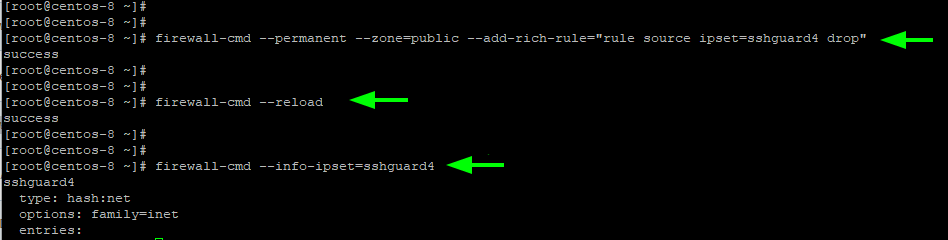
Automation to Block Brute-force Attacked IP detected by Microsoft Defender for Cloud - Microsoft Community Hub

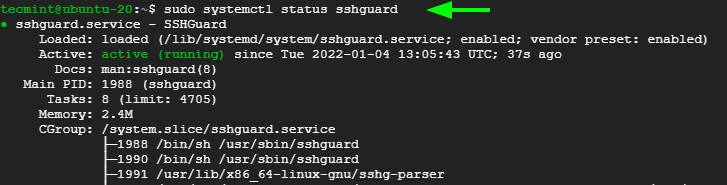
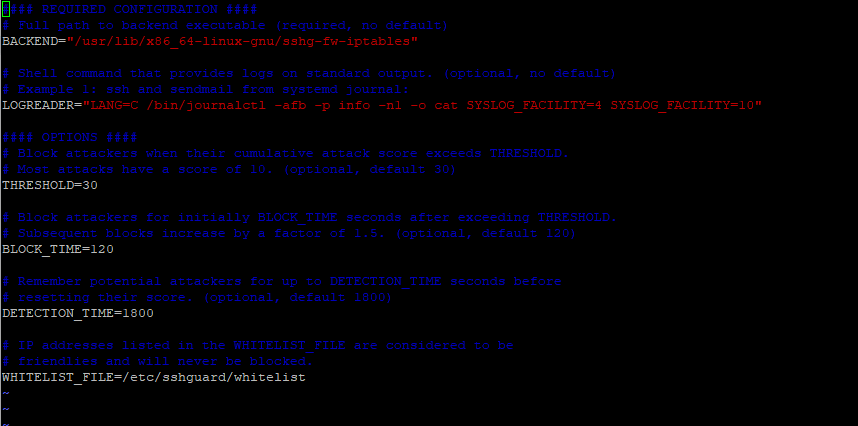
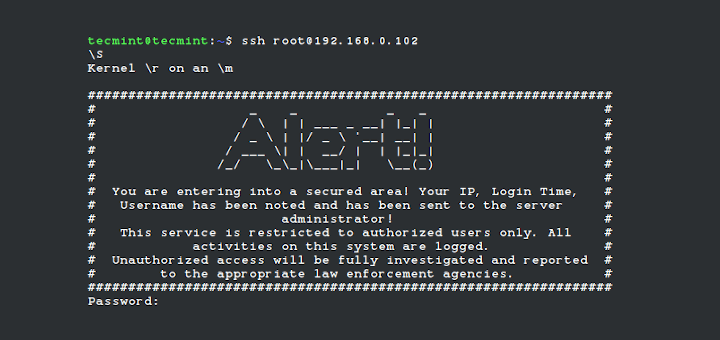
How Do I Block Brute-Force Attacks?_Host Security Service (Old)_ User Guide (ME-Abu Dhabi Region) _FAQs_Alarm and Event Management_Brute-force Attack Defense_Huawei Cloud

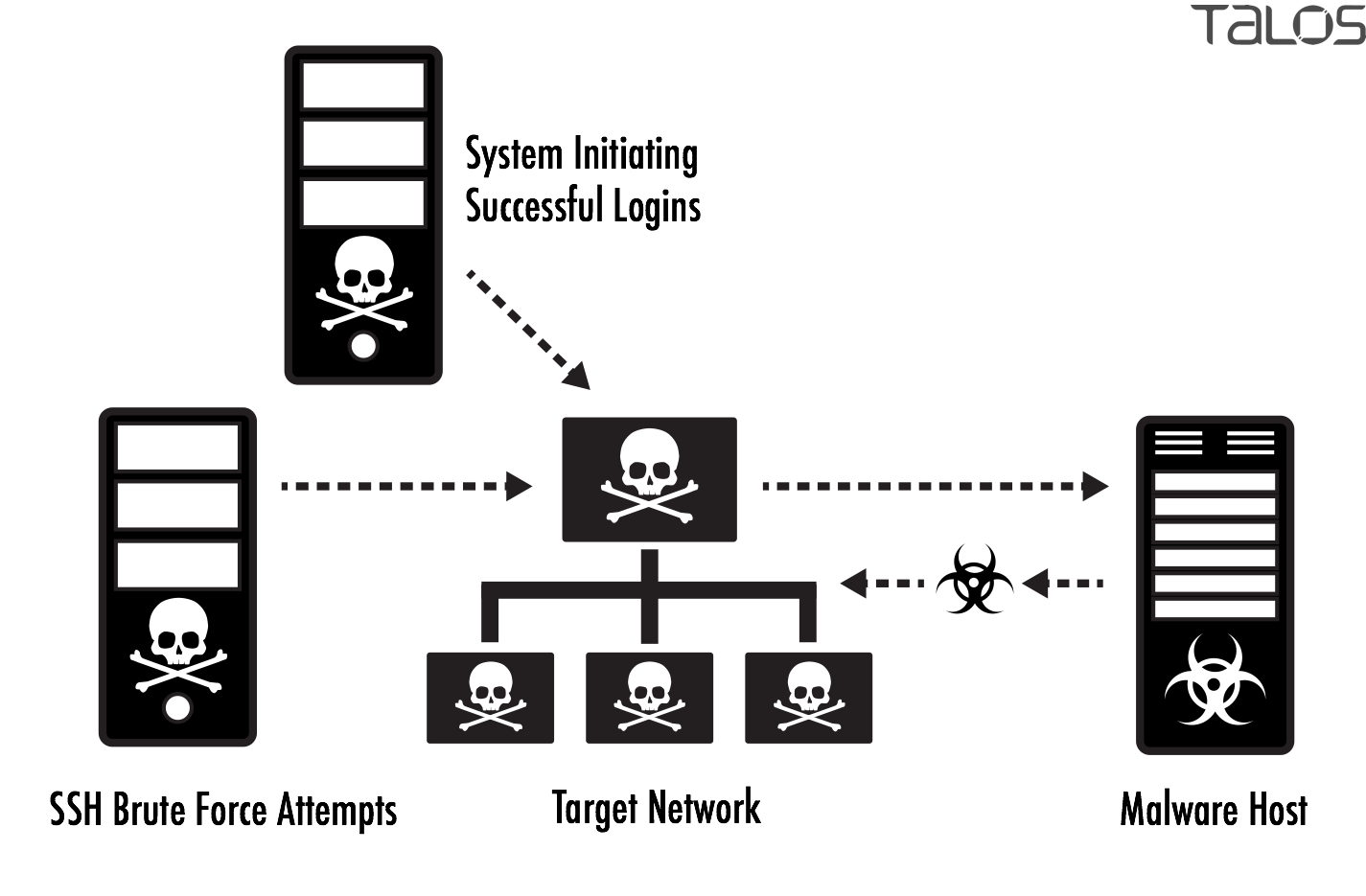
Automation to Block Brute-force Attacked IP detected by Microsoft Defender for Cloud - Microsoft Community Hub